MeetrixIO team is well experienced with WebRTC related technologies. We provide commercial support for Jitsi Meet, Kurento, OpenVidu, BigBlue Button, Coturn Server and other webRTC related open-source projects.
How Jitsi VideoBridge 2 Handles WebRTC Traffic
Jitsi Videobridge has the ability to handle webRTC traffic over UDP as well as over TCP.
By default JVB uses UDP, ports 10000 - 20000 for Media Traffic. If client's firewall has no restrictions on these UDP ports, default Jitsi Meet setup should work without any issues. In case if the client's firewall has restrictions on UDP traffic, you can configure videobridge to use a TCP connection between the client behind the firewall and the Videobridge as a fallback (In other words, you can instruct the JVB to consider TCP candidate pairs).
4 Ways that you can Configure Media Traffic over TCP with JVB
JVB on port 4443 (For single server installations)
If you have all the jitsi meet components on the same server, the web server (Nginx, Apache or Tomcat) which serves the frontend will occupy the port 443. I this case, we can configure the Jitsi Video Bridge (JVB) to use port 4443 for webRTC Media traffic over TCP. To do that you have to add the following line to /etc/jitsi/videobridge/sip-communicator.properties in JVB.
org.jitsi.videobridge.DISABLE_TCP_HARVESTER=false
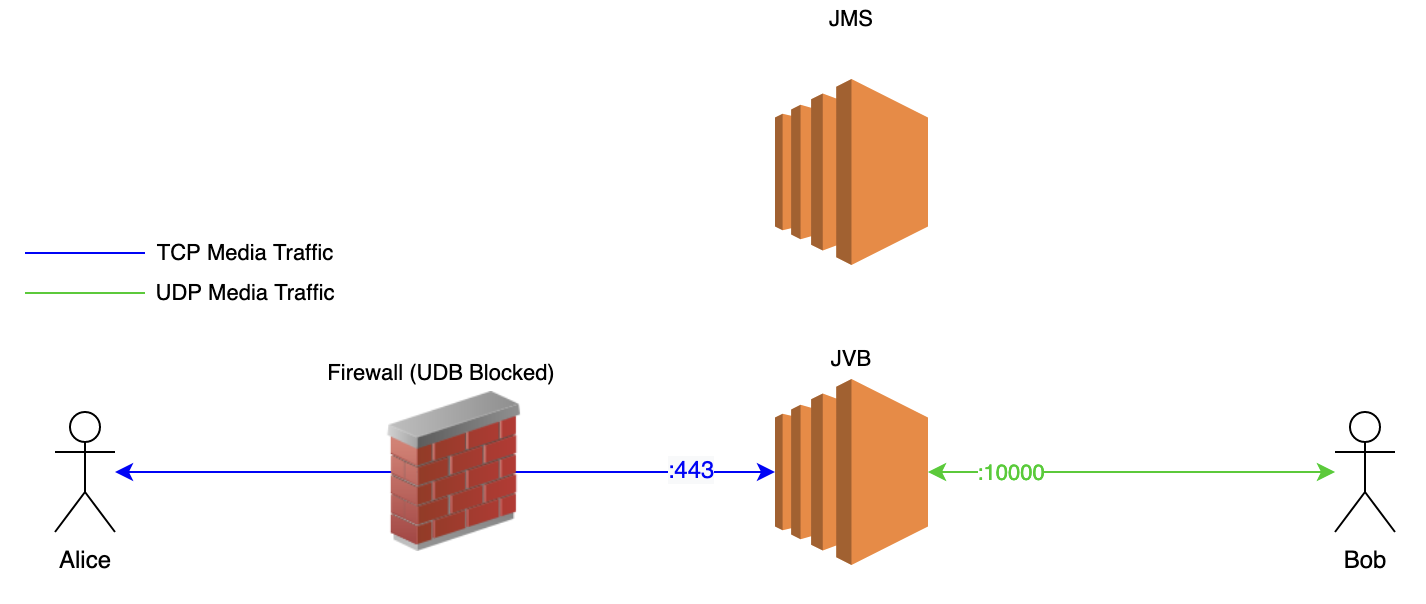
Some strict firewalls do not allow anything other than TCP 80 and 443 for incoming/outgoing traffic. In those cases, this might not work for you.
Nginx Multiplexing with Coturn (For single server installations)
If you really want to keep all the Jitsi components on a single server and do not want to install JVB on a separate server, Nginx which runs on port 443 can be configured to forward the TCP media traffic to Coturn server and then, the Turn server should relay the media to JVB via UDP.
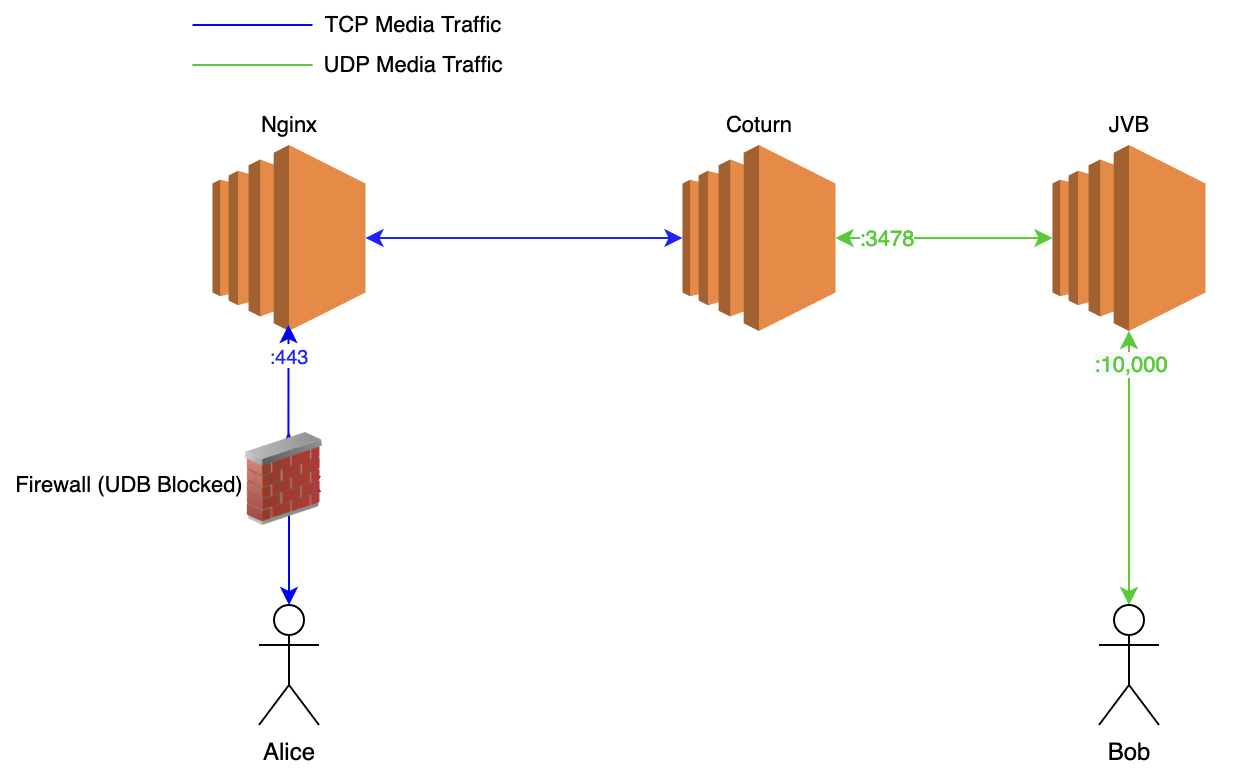
You can follow (this guide)[https://jitsi.github.io/handbook/docs/devops-guide/turn] implement this.
Some of the older quick installations used this as the default configuration. If you can find a file in /etc/nginx/modules-enabled/60-jitsi-meet.conf your setup is already configured in this way. But this setup is bit troublesome. The best solution would be to use separate servers for JVBs.
JVB on a Separate Server
If you install JVB on a separate server, JVB can be configured use port 443 for TCP media traffic by adding following line to /etc/jitsi/videobridge/sip-communicator.properties in JVB.
org.jitsi.videobridge.DISABLE_TCP_HARVESTER=false

This is a very straightforward solution
Turn server on a Separate Server
If you are using an Autoscaling mechanism and if each JVB gets a dynamic IP while auto scaling and if you need to whitelist the IP Addresses of the media servers in a corporate firewall, you can use a Turn server (In other words, you can use relay candidates).
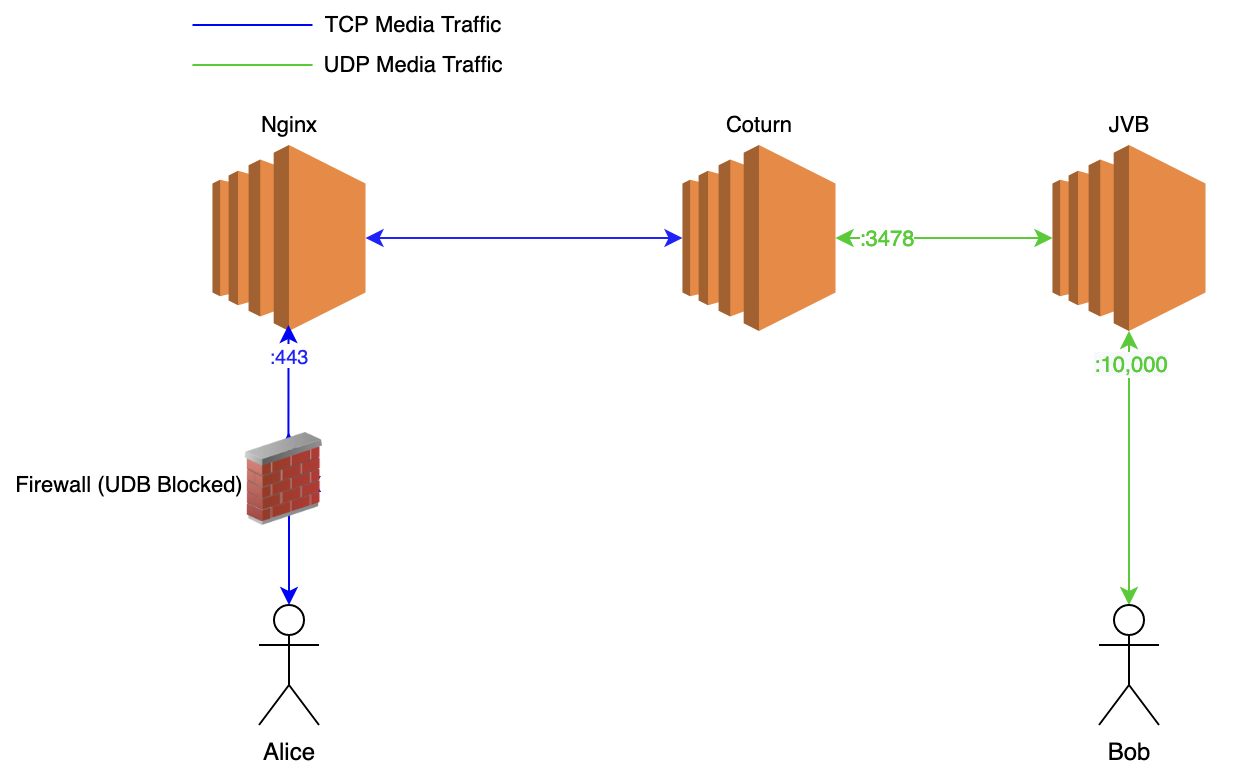
In this way, you can have a fixed number of Turn servers and whitelist their IPs in your Firewall while JVBs are using dynamic IPs. You can follow Setting up a Turn Server for Jitsi Meet guide to setup a Turn Server with tls support to relay media traffic.
Looking for commercial support for Jitsi Meet ? Please contact us via hello@meetrix.io

Leave a Comment